|
|
Programmable In-network Security (Poise)
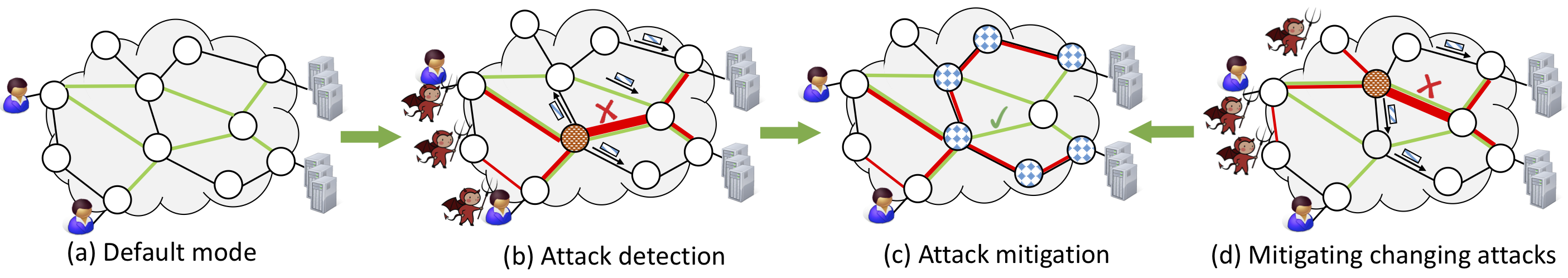
Poise, or Programmable In-network Security, aims to rethink how to make our future networks fundamentally more secure.
Our observation is that many network-based attacks should be mitigated inside the network (instead of at endpoints),
but traditional networks can only support simple defenses because they lack programmability.
With programmable switches, we can now develop attack detection algorithms in hardware to process every single packet at high speed.
Upon detecting an attack, the defense can directly take actions at the switch without involving a software controller.
Our vision for Poise is to transform the network into a "programmable defense infrastructure" that can support security as routing.
Concretely, a Poise switch not only forwards traffic, but also applies
to it a wide range of defenses; a Poise network not only routes traffic end-to-end, but also swaps
defenses along the paths in and out as needed to mitigate attacks. Attacks with mixed vectors would trigger concurrent defenses,
and attacks that rapidly change would be met with equally fast defense swapping. In its full force, Poise would toggle a wide
array of defenses rapidly on and off as traffic flows through, mitigating attacks in real time.
We're taking three steps to realize this Poise vision, as detailed below.
1. The switch as a defense platform
Our first step is to transform a programmable switch into a defense platform that runs a wide range of "defense apps".
The key challenge lies in the limited programming model and resources in a network switch. Our key solution is to
leverage software/hardware codesign, which divides a defense app into a hardware component that needs to be invoked
per packet, a software component that only needs to be involved per batch, and an interface that permits bi-directional
communications.
NetWarden [USENIX Security 2020]
outlines design principles for software/hardware codesign for network security applications.
It applies these design principles to a concrete use case: mitigating network covert channels.
Poise [USENIX Security 2020]
is an advanced access control system for "context-aware" security.
Poise comes with a high-level policy language, with which users can easily specify a wide range of context-aware policies. Our compiler then
generates switch programs that implement these policies entirely in hardware.
2. The network as a defense fleet
Our next step aims to transform a programmable network into a defense fleet, by architecting the individual defenses developed in the
first step into the network paths, and synchronizing them for network-wide attack detection and mitigation. The key challenge
we need to tackle is decentralization: the defenses need to synchronize their local views and decisions with each other without
going through a central controller.
FastFlex [HotNets 2019][USENIX Security 2021]
outlines the approach that we're taking to this decentralized defense design. It proposes the abstraction of a
multimode data plane, which normally operates in an optimal mode, but can enter and exit defense modes at RTT timescales
upon attacks.
3. Securing the defenses
Last but not least, Poise seeks to ensure that the individual defenses, as well as their composition, are themselves secure
against attacks. We are developing program analysis techniques to understand potential risks in the defenses and mitigate them.
Automated attack discovery [CSET 2019][ASPLOS 2021]
describes a new class of attack vectors to systems that rely on programmable switches, and outlines steps towards
discovering the attack vectors automatically.
Publications
-
Ripple: A Programmable, Decentralized Link-Flooding Defense Against Adaptive Adversaries
Jiarong Xing, Wenqing Wu, and Ang Chen
USENIX Security 2021 [PDF]
-
Probabilistic Profiling of Stateful Data Planes for Adversarial Testing
Qiao Kang, Jiarong Xing, Yiming Qiu, and Ang Chen
ASPLOS 2021 [PDF]
-
NetWarden: Mitigating Network Covert Channels while Preserving Performance
Jiarong Xing, Qiao Kang, and Ang Chen
USENIX Security 2020 [PDF] [Code]
-
Programmable In-Network Security for Context-aware BYOD Policies
Qiao Kang, Lei Xue, Adam Morrison, Yuxin Tang, Ang Chen, and Xiapu Luo
USENIX Security 2020 [PDF] [Code]
- Architecting Programmable Data Plane Defenses into the Network with FastFlex
Jiarong Xing, Wenqing Wu, and Ang Chen
HotNets 2019 [PDF]
- Automated Attack Discovery in Data Plane Systems
Qiao Kang, Jiarong Xing, and Ang Chen
CSET 2019 [PDF]
- NetWarden: Mitigating Network Covert Channels without Performance Loss
Jiarong Xing, Adam Morrison, and Ang Chen
HotCloud 2019 [PDF]
- Enforcing Context-Aware BYOD Policies with In-Network Security
Adam Morrison, Lei Xue, Ang Chen, and Xiapu Luo
HotCloud 2018 [PDF]
| |
|
